Federating Azure AD Users Accessing AWS
- Assign Azure AD Users to AWS IAM Role, in Azure AD Portal select Users and groups
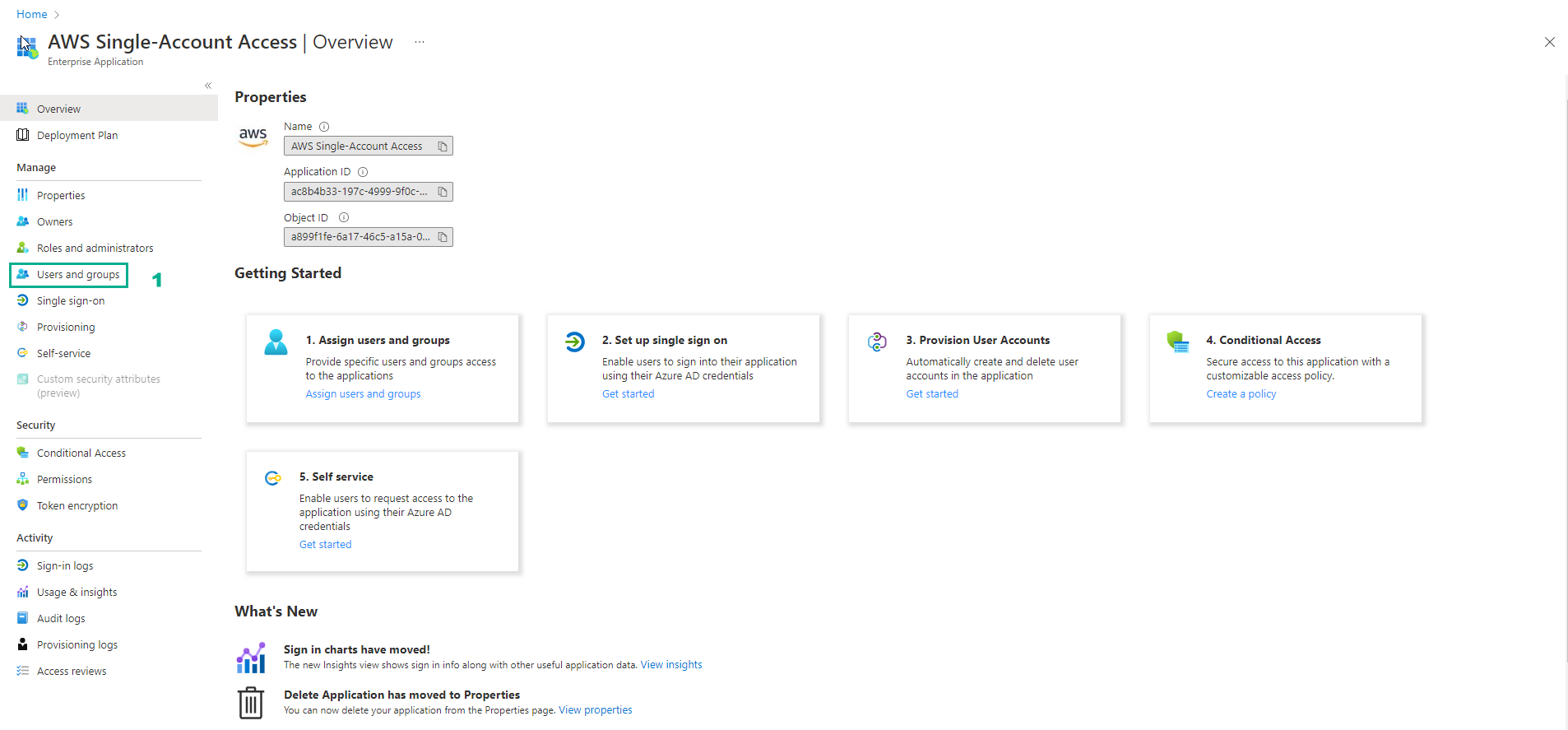
- Select Add user/group
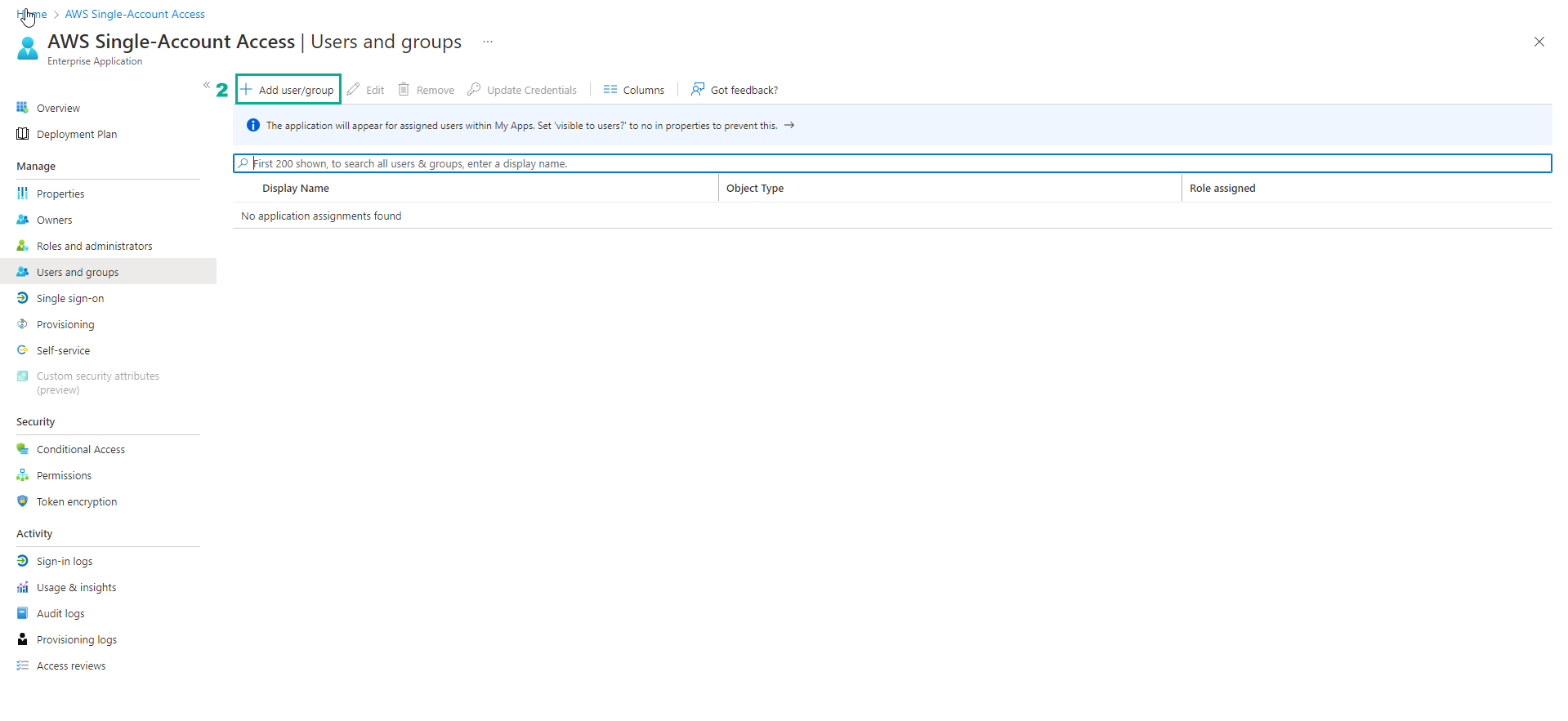
Note: For AWS Roles to show up in the next step, you may have to wait 5-10 minutes. And to use the feature of assigning AWS IAM Roles to Azure by Group, you need to upgrade your Azure plan.
- In the Add Assignment page
- Select Users, a list of Users will appear on the right
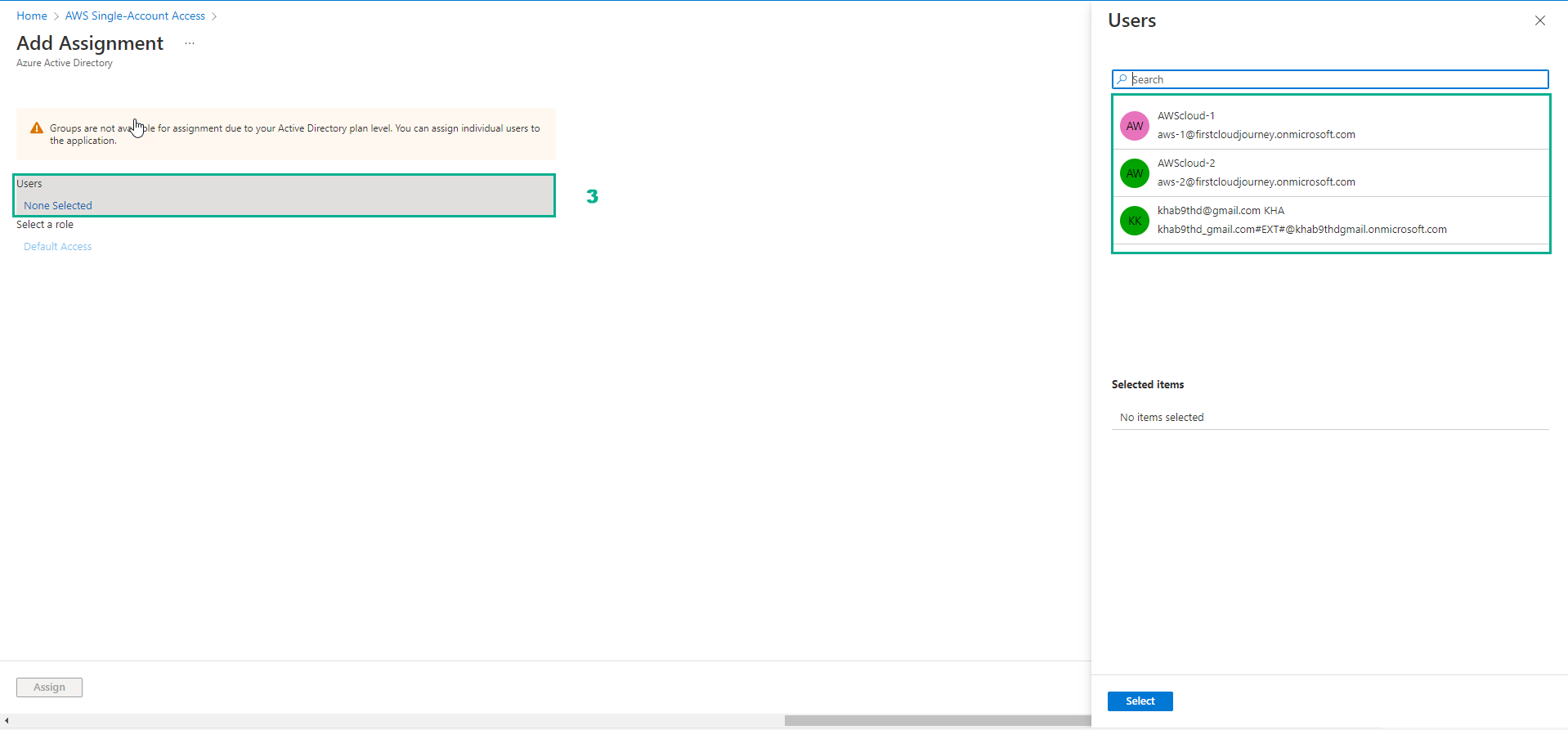
- Select the user name (eg AWScloud-1) and select Select
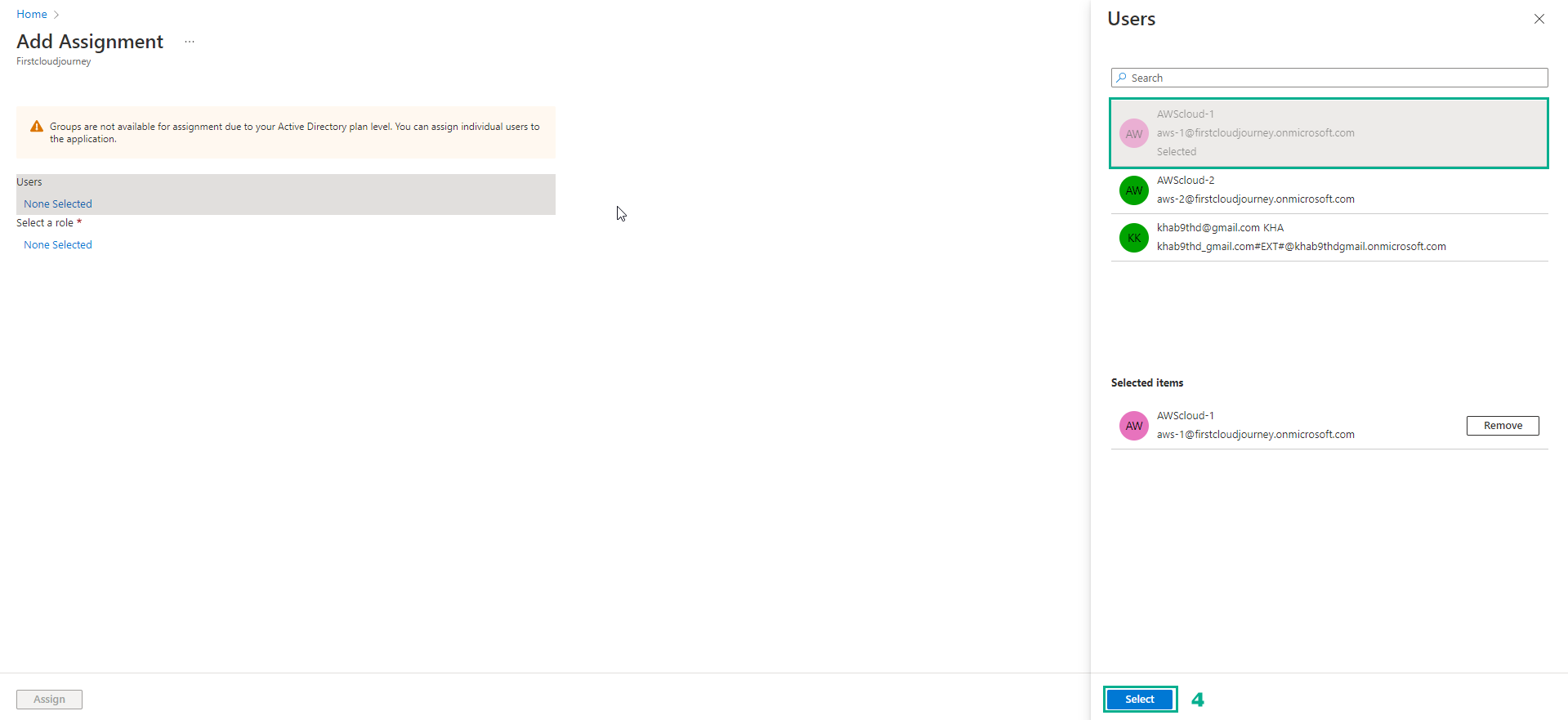
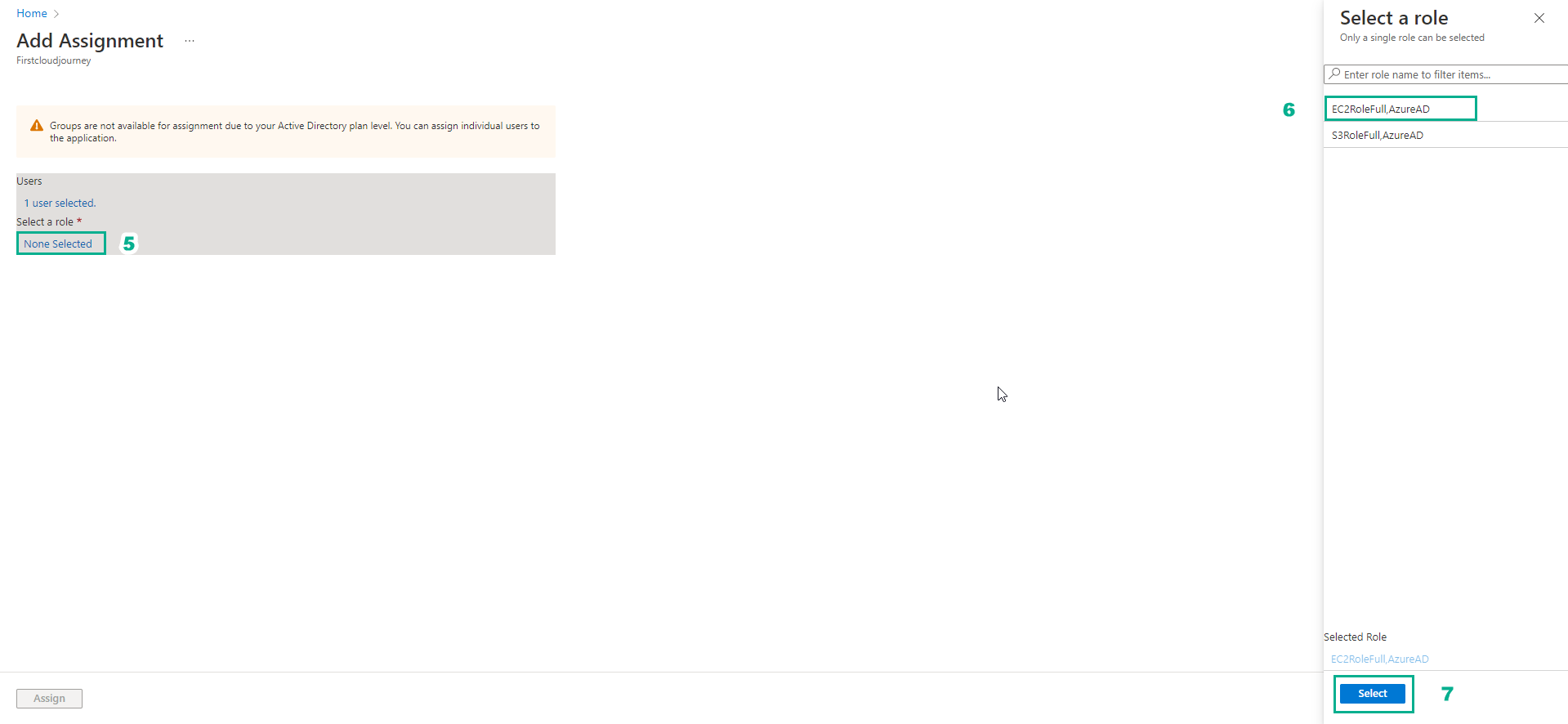
- In the Select a role section, select None Select to select the User Role AWScloud-1
- Select EC2RoleFull
- Select Select
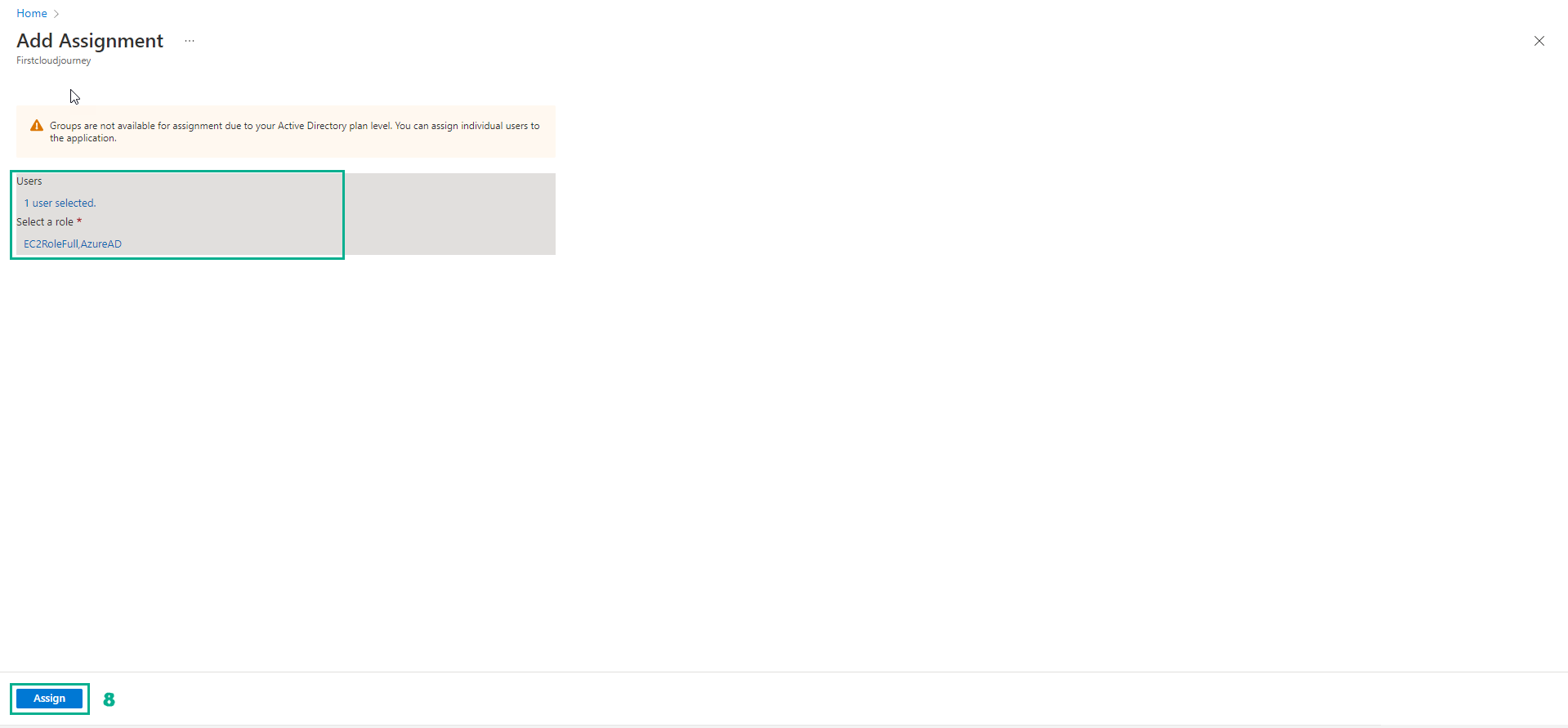
- Select Assign
- You iterate and assign User AWScloud-2 to S3RoleFull.
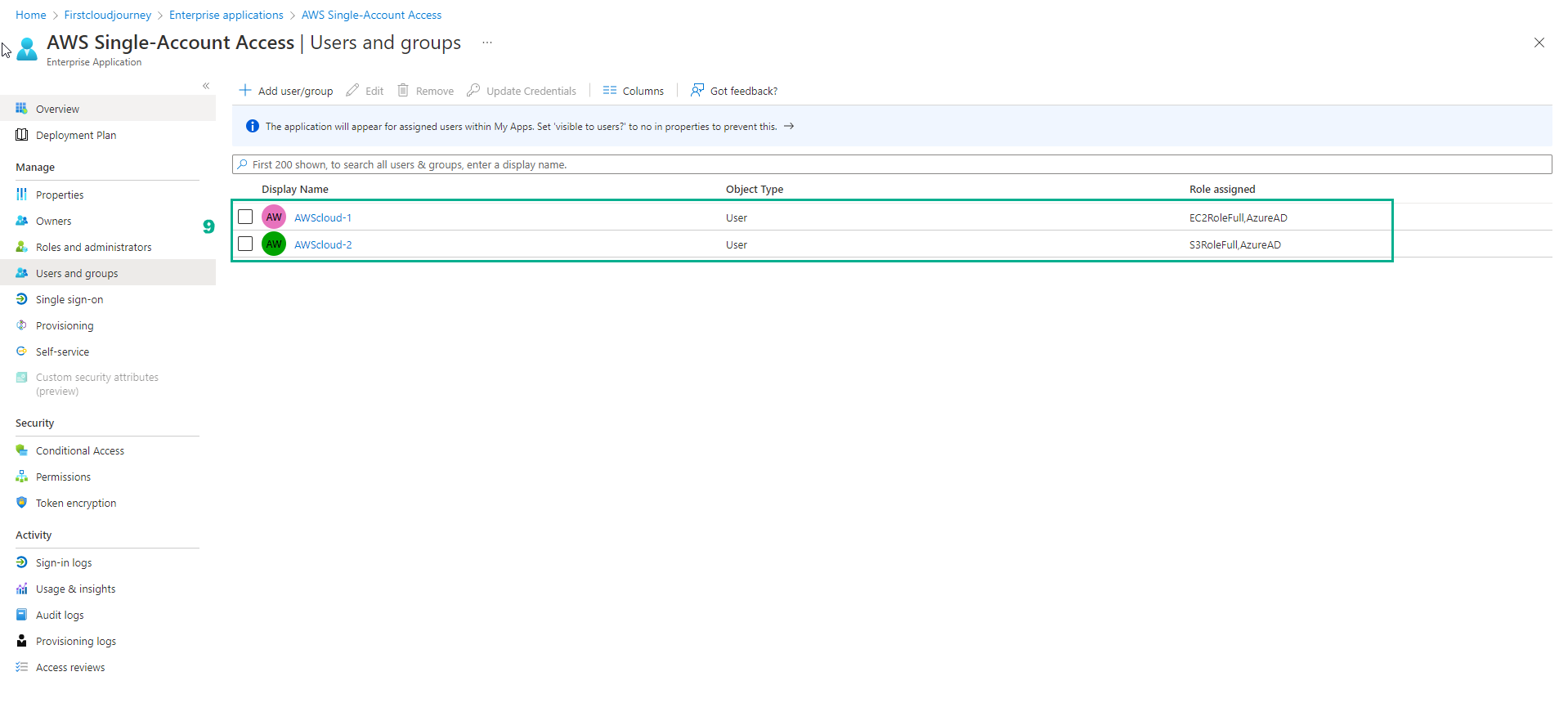
So you have created a user in Azure AD and connected to AWS through the Identity Provider.